
Technology continues to enable greater collaboration, fuel the creativity of both students and educators, and make the sharing of ideas easier than ever. In addition, the convenience with which we store data in high-availability, connected systems enhances the ability of individuals, classrooms, and teams to create and learn. Along with these benefits, come challenges. Administrators face the task of creating safe and secure computing environments for their students and faculty.
This was the focus of a panel — “Creating a secure and safe online environment for all students” — at the annual California Educational Technology Professionals Association (CETPA) conference this November in Pasadena, California. K-12 leaders including educators, administrators, industry representatives, and technology professionals gathered in a session that explored holistic digital citizenship strategies, steps to protect data systems, and approaches to secure online resources and devices.

Members of the panel included:
- Richard Quinones, Sr. VP of SLED (State, Local and Education), iboss
- Rick Miller, Former Superintendent, Santa Ana USD
- Bryant Wong, CTO, Summit Public Schools
- Ron Chandler, Former CIO, LAUSD and current CIO, UCLA Anderson School of Business
- Julie Evans, CEO, Project Tomorrow
“There’s been this explosion in terms of student data, an explosion in terms of teachers using different types of digital content, an explosion in the use of mobile devices, an explosion in the use of cloud applications and the move to cloud, and all of that has created some really interesting challenges,” said Julie Evans, CEO of Project Tomorrow, an organization that advocates for the use of technology to ensure students become tomorrow’s innovative, engaged citizens and leaders.
In the Age of Cloud Computing, Protecting the Castle Is Not Enough
At many organizations, the traditional approach to security has been the “perimeter”-based defense that relies on technology, operated by specialized staff. The idea is to protect the castle with a moat, and use a drawbridge to control the flow of all incoming and outgoing information. The responsibility of protecting the castle falls solely on the technology team.
In today’s distributed and highly connected environments, however, this approach is insufficient. Also, many breaches originate from phishing attacks and lost or stolen equipment. Essentially, protecting the castle isn’t enough anymore because the data is stored at too many other locations as well. And if folks in the castle unwittingly give up their passwords, the moat offers no protection at all.
Strategic, Tactical, and Measurable Ways to Manage Risk
When we look at a typical implementation of perimeter-based security, we find it to be comprised of tools such as specialized hardware and software, and systems with policies designed to compartmentalize information in order to protect access to it. What’s absent in this approach is people, and their awareness of the role they play in guarding sensitive data. While the traditional protection mechanisms help, raising awareness and educating individuals (in any role) are critical elements in shoring up the security posture of any organization.
“As an organization, we transformed from one where security wasn’t at the top of folks’ minds to one where it’s at the top of their minds, because everyone is involved. Everyone gets it,” said Bryant Wong, CTO of Summit Public Schools. “Our security working group cuts across all teams: our External Engagement Team, our Schools Team, our Talent Team, our Legal Team, our Analytics Team, they’re all involved, and they all have an equal voice in shaping [the strategy]. It’s not just IT coming up with it.”
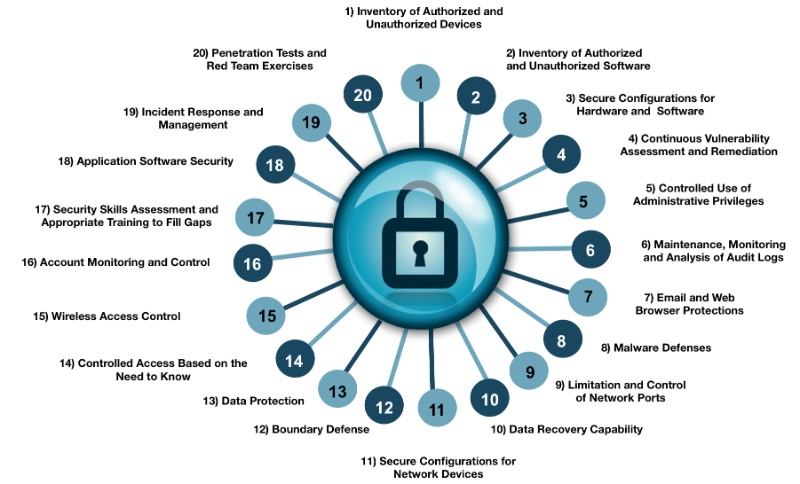
Along with the strategic element of individual contributions to security, Summit is introducing changes at the tactical level in order to measure and manage risk. The traditional mechanisms for protecting the castle are still relevant, but we can gauge the effectiveness of those mechanisms and measure the outcomes of a security program. By adopting the Center for Internet Security’s Critical Security Controls (CSC) and using each control to measure the risk associated with them, an organization will find it has levers it can pull to help decide how to allocate resources in ways that protect the most important systems and data.
Digital Safety: An Essential, Shared Responsibility
As technology continues to evolve, the importance of digital safety will grow. At Summit, the individuals leading the way in implementing its security strategy aim to not only protect student and organizational data, but to fulfill Summit’s greater responsibility in educating our community about the importance of practicing digital safety, whether at work, school, or home.
“What does awareness look like when we talk about data security and data privacy?” Wong said. “How do we make sure we understand what that means, not just for the workplace, but how do we take those lessons learned home, and share it with friends and family, and take ownership of it?”
“Part of technology’s job is not to come down with a mandate on how to do security, but to bring it about in a way that allows everyone to be part of the conversation, to share in the responsibility of securing the organization and to share our security measures.”
This post provides a summary of the CETPA panel on “Creating a secure and safe online environment for all students.” To watch the entire panel discussion, visit our YouTube page.

